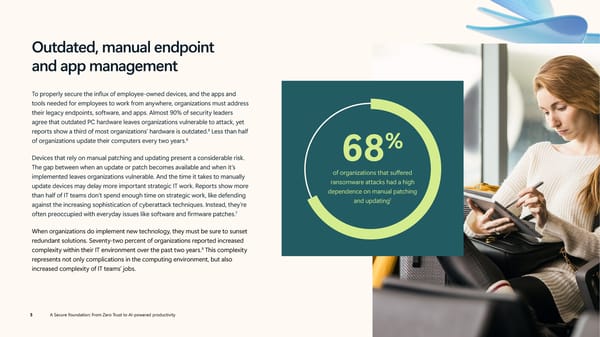
Outdated, manual endpoint and app management To properly secure the influx of employee-owned devices, and the apps and tools needed for employees to work from anywhere, organizations must address their legacy endpoints, software, and apps. Almost 90% of security leaders agree that outdated PC hardware leaves organizations vulnerable to attack, yet reports show a third of most organizations’ hardware is outdated.8 Less than half of organizations update their computers every two years.8 % Devices that rely on manual patching and updating present a considerable risk. 68 The gap between when an update or patch becomes available and when it’s implemented leaves organizations vulnerable. And the time it takes to manually of organizations that suffered update devices may delay more important strategic IT work. Reports show more ransomware attacks had a high than half of IT teams don’t spend enough time on strategic work, like defending dependence on manual patching 7 against the increasing sophistication of cyberattack techniques. Instead, they’re and updating 7 often preoccupied with everyday issues like software and firmware patches. When organizations do implement new technology, they must be sure to sunset redundant solutions. Seventy-two percent of organizations reported increased complexity within their IT environment over the past two years.9 This complexity represents not only complications in the computing environment, but also increased complexity of IT teams’ jobs. 5 A Secure Foundation: From Zero Trust to AI-powered productivity
 A secure foundation Page 4 Page 6
A secure foundation Page 4 Page 6